Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
Quickbooks Customer Service Number +1(888)262-4180 Endpoints act as entrance points into an enterprise community and provide avenues for malevolent actors to take advantage of. These points of entry are shielded against dangerous endeavors and/or malevolent attacks by endpoint protection software. Agencies can maintain greater control over the growing number of different types of network access factors when they are able to guarantee endpoint adherence to records security standards. Testing your organization’s cyber security on a regular basis is crucial since cybercriminals are constantly improving their tools, strategies, and techniques for breaking into networks.
Are you keeping up your online hygiene? The term “cyber hygiene” describes the procedures and actions taken by every employee of a company using a computer or other device to preserve and enhance their security both online and off. These procedures are frequently used on a regular basis to protect identification and other information that might be compromised or stolen. Cyber hygiene recommended practices help safeguard the network and assets of your company, just as personal hygiene habits assist you keep yourself healthy. Here’s where we can help. Our entire company is set up to make this challenging situation easier, more straightforward, and less ostentatious for our clients.
📞 Quickbooks Customer Service Number 📞+1-888-262-4180 📞
6srt Ways Live Quickbooks to Intuit Payroll Number Solve Your Error USA jkjljoijkljjkluijkluklnjklu
Posted by
–
Follow Us
Recent Posts
Tags
#technology airline airlines american airlines customer service anti-virus asacc sdca business Chat Coinbase coinbase support number Crypto.com support number Email Expedia expedia customer service faq fashion helping Jetblue norton or Chat Options: Step by Step Guide qb quickbooks QuickBooks Payroll Support Number Service Support travel travels UnitedAirlines United Airlines werty




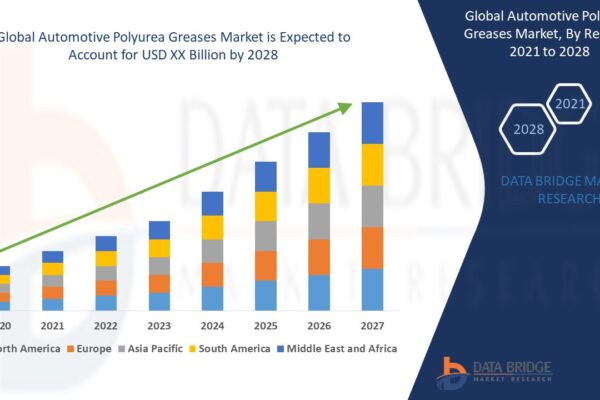
Leave a Reply
You must be logged in to post a comment.